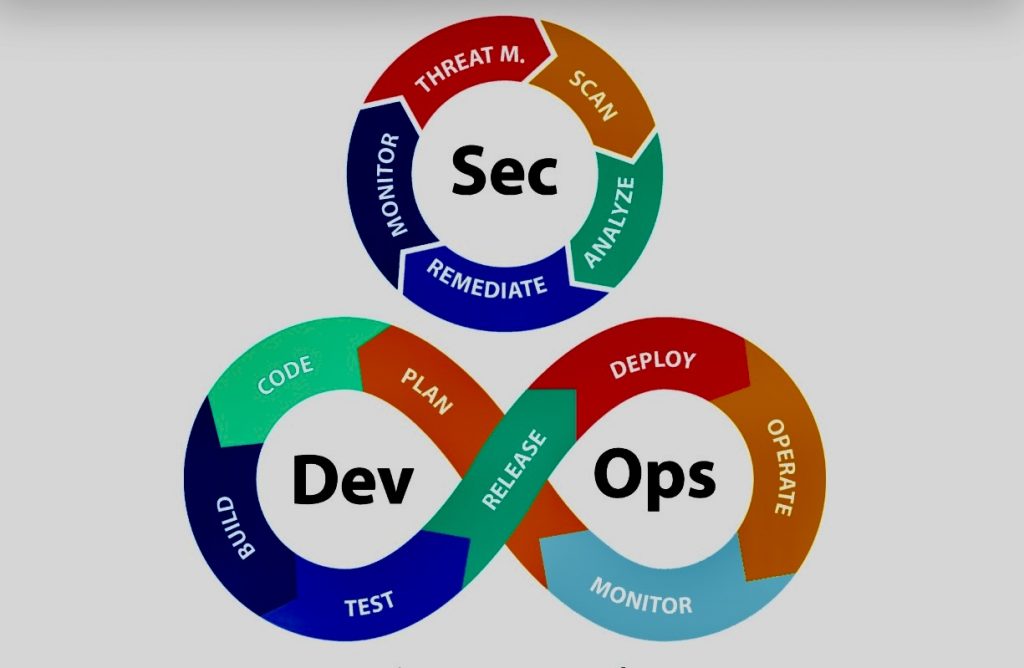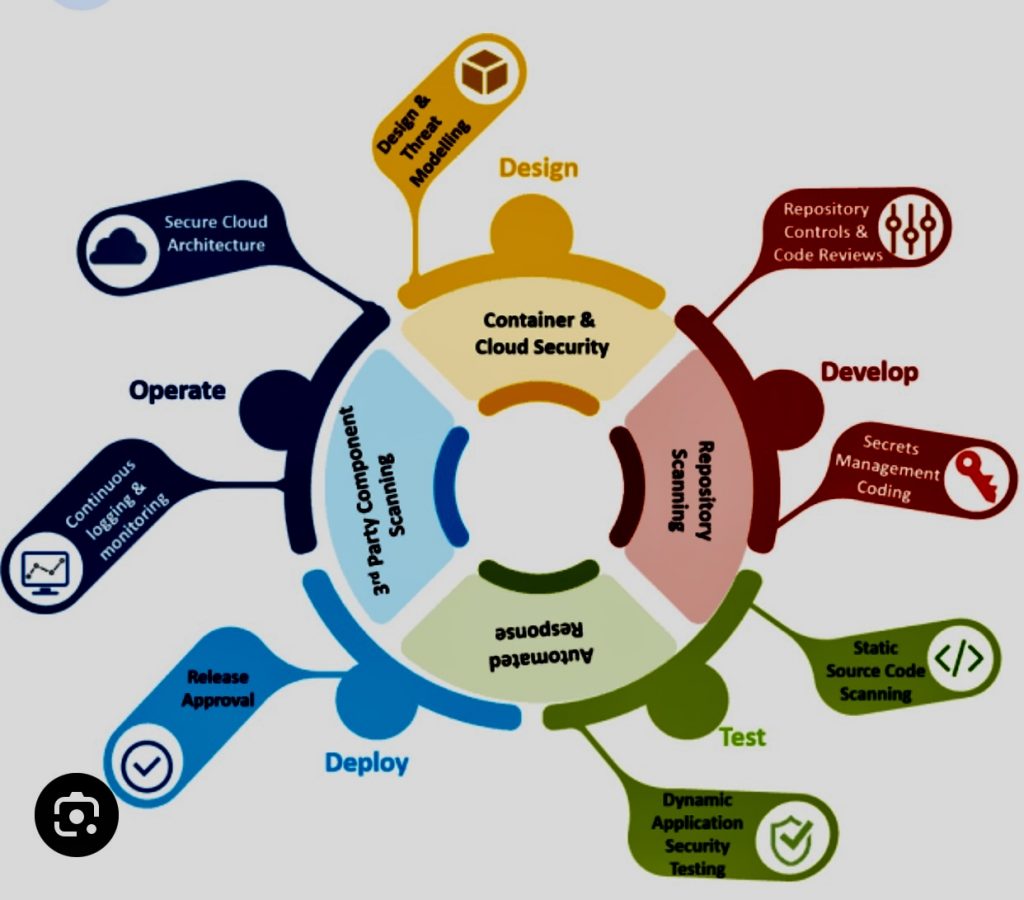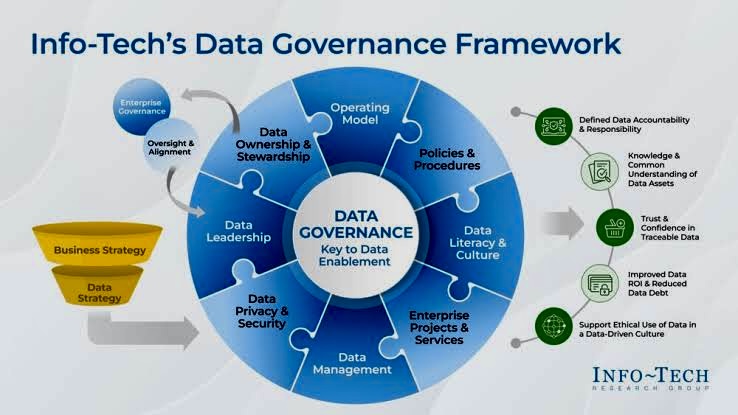
Key Performance Indicators (KPIs) are essential ways of measuring the progress and success of business programs, including a data governance program.
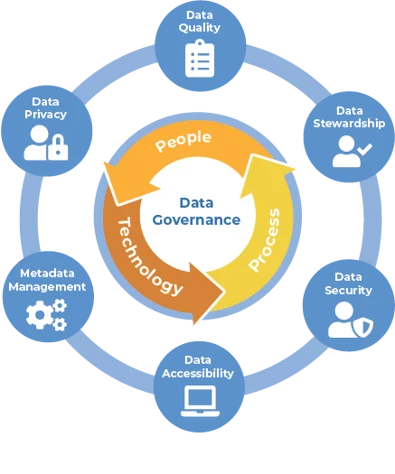
Effective Data Governance hinges on measuring and monitoring progress through key performance indicators (KPIs).
Choosing the right KPIs depends on your specific program goals and priorities, but here are some top contenders:
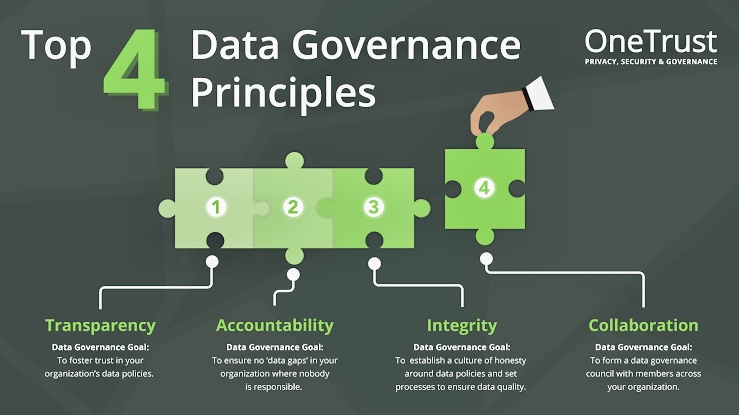
A. Data Quality:
o Accuracy: Percentage of data records that are correct and free from errors.
o Completeness: Percentage of data records that have all required information.
o Timeliness: Percentage of data that is available when needed and updated with relevant changes.
o Consistency: Degree of uniformity and coherence across different data sources and systems.
o Validity: Percentage of data that conforms to defined rules and business context.
B. Data Access and Incidents:
o Access Control Effectiveness: Measures how well access controls are preventing unauthorized access to sensitive data.
o Incident Response Time: Tracks the time taken to respond to and resolve data security incidents.
C. Data Security and Compliance:
o Number of data breaches or security incidents.
o Percentage of data access requests handled within defined timelines.
o Regulatory Compliance: Ensures adherence to data protection regulations and industry-specific compliance requirements. (e.g., GDPR, CCPA).
o Audit Findings: Monitors findings and recommendations from internal and external audits related to data governance.
o Time taken to identify and remediate data security vulnerabilities.
D. Data Usage and Value:
o Number of users actively accessing and utilizing data.
o Frequency and success rate of data-driven decision-making initiatives.
o Return on investment (ROI) of data analytics projects and initiatives.
o Increase in revenue, cost savings, or other business benefits attributed to data usage.
E. Data Stewardship:
o Stewardship Engagement: Measures the active participation and involvement of data stewards in maintaining data quality and integrity.
o Stewardship Issue Resolution Time: Tracks the time taken to resolve data-related issues identified by data stewards.
F. Metadata Management:
o Metadata Accuracy: Assesses the accuracy of metadata, ensuring it correctly describes the associated data.
o Metadata Completeness: Measures the extent to which metadata covers all relevant aspects of the data.

G. Data Lifecycle Management:
o Percentage of data records properly classified and labeled.
o Time taken to archive or delete outdated or irrelevant data.
o Efficiency of data backup and recovery processes.
o Effectiveness of data retention policies in meeting legal and regulatory requirements.
o Data Retention Compliance: Ensures that data is retained and disposed of according to legal and regulatory requirements.
o Data Archiving Efficiency: Measures the effectiveness of data archiving processes in preserving historical data.
H. Data Governance Adoption:
o Training Completion Rates: Tracks the completion rates of data governance training programs among relevant stakeholders.
o Policy Acknowledgment: Measures the acknowledgment and acceptance of data governance policies by employees.
I. Business Impact:
o Data-Driven Decision-Making Improvement: Assesses the improvement in decision-making processes due to enhanced data quality and availability.
o Cost Reduction: Measures the reduction in costs associated with data-related issues and inefficiencies.
J. Data Usage Metrics:
o Data Utilization: Tracks how frequently and effectively data is being used for business purposes.
o Data Consumption Trends: Monitors trends in data consumption patterns and identifies areas of high demand.
K. Data Governance Maturity:
o Maturity Assessment Scores: Periodic assessments of the organization’s data governance maturity level.
o Progress in Program Initiatives: Tracks the successful completion of planned data governance initiatives.
L. Governance Processes and Effectiveness:
o Adoption rate of data governance policies and procedures.
o Timeliness and accuracy of data governance reporting.
o Level of stakeholder engagement and satisfaction with the Data Governance program.
o Effectiveness of training and awareness programs for data governance principles.
M. Data Availability:
o Is the necessary data accessible and readily available for all relevant stakeholders within the organization when needed? This is often an important element of a successful data governance program.
N. Data Literacy:
o How well do employees understand the data? This KPI aims at measuring the level of understanding and ability of staff to use data effectively.
O. Ease of Data Integration:
o If data is easily integrated from different sources and platforms, it shows effective data governance.
P. Improvement Over Time:
o Is the data quality and reliability improving over time? A successful data governance program should see a trend towards improvement in all KPIs.
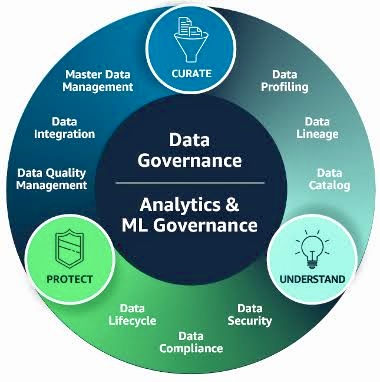
Q. Stakeholder Satisfaction:
o Measuring stakeholder satisfaction, either through surveys or interviews, gives an indication of whether the program is meeting the needs of the users.
R. Data Sharing and Collaboration:
o The degree to which data is shared and collaborated on within the organization, measured by usage metrics, can be a good indicator of a healthy data governance program.
Additional recommendations:
o Align KPIs with program goals: Clearly define your Data Governance objectives and choose KPIs that directly measure progress towards those goals.
o Balance quantitative and qualitative measures: While numbers are important, consider also metrics like user feedback and perceived improvements in data quality and access.
o Track KPIs regularly and consistently: Monitor your KPIs over time to identify trends, assess progress, and make adjustments to your Data Governance program as needed.
o Communicate results transparently: Share KPI results with stakeholders to increase awareness, build trust, and demonstrate the value of the Data Governance program.
Key Performance Indicators (KPIs) play a crucial role in assessing the effectiveness and success of a Data Governance program. The specific KPIs can vary based on organizational goals and the nature of the data being managed.
Customizing these KPIs to align with specific organizational objectives and industry requirements is crucial. Regularly reviewing and updating KPIs ensures that they remain relevant and contribute to the continuous improvement of the Data Governance program.
https://www.edq.com/blog/data-governance-metrics-kpis-to-measure-success/