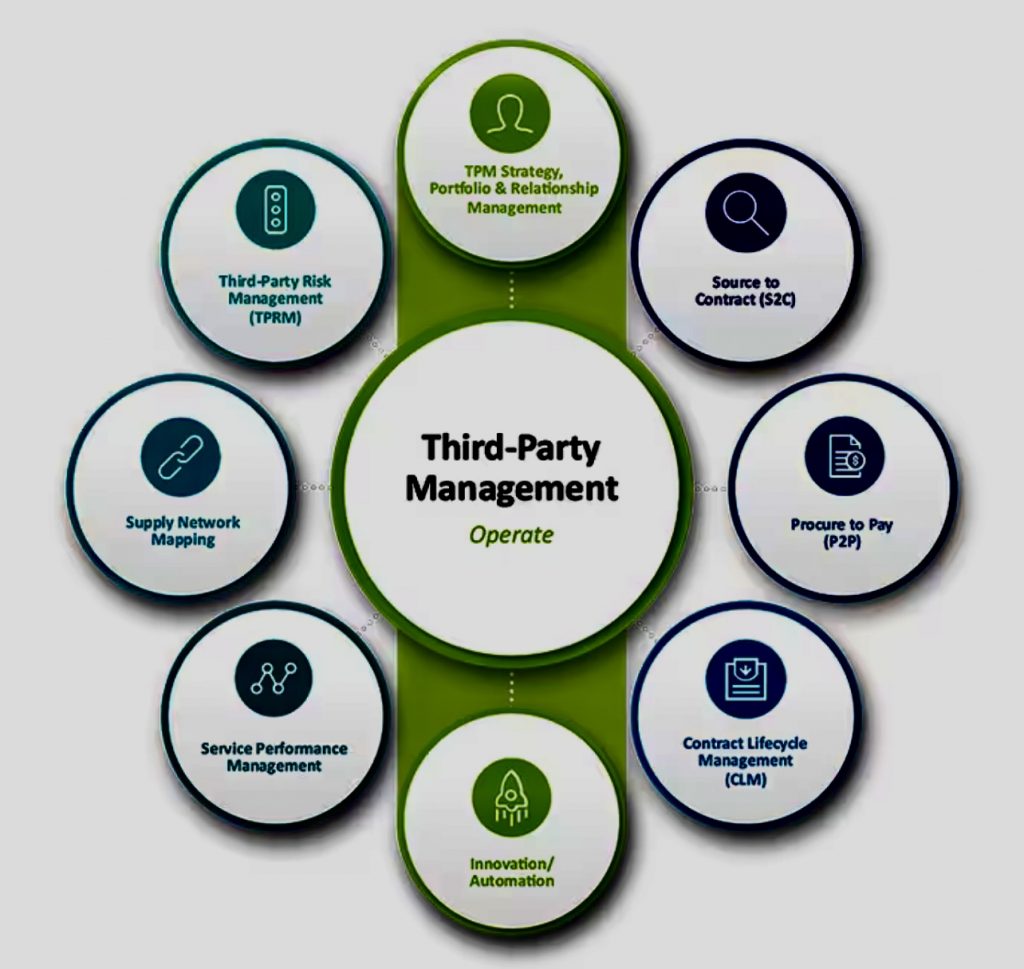
Third-party vendors play a crucial role in today’s interconnected business landscape, providing a wide range of services and expertise to organizations.
However, this reliance on external partners also introduces a layer of complexity and potential risks that organizations must carefully manage. Hidden risks associated with third-party vendors can have significant consequences, including data breaches, financial losses, and reputational damage.
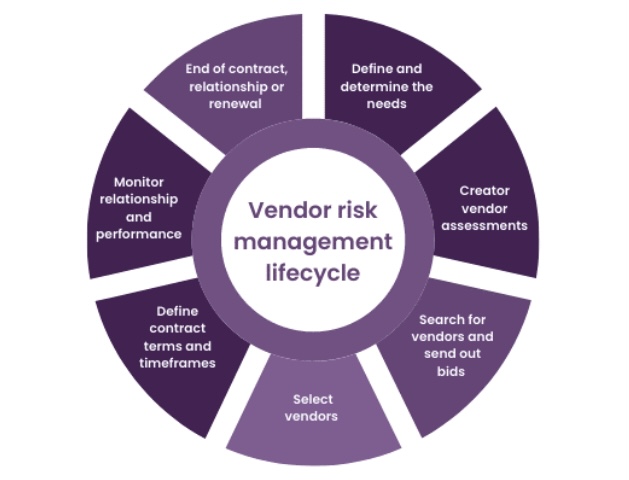
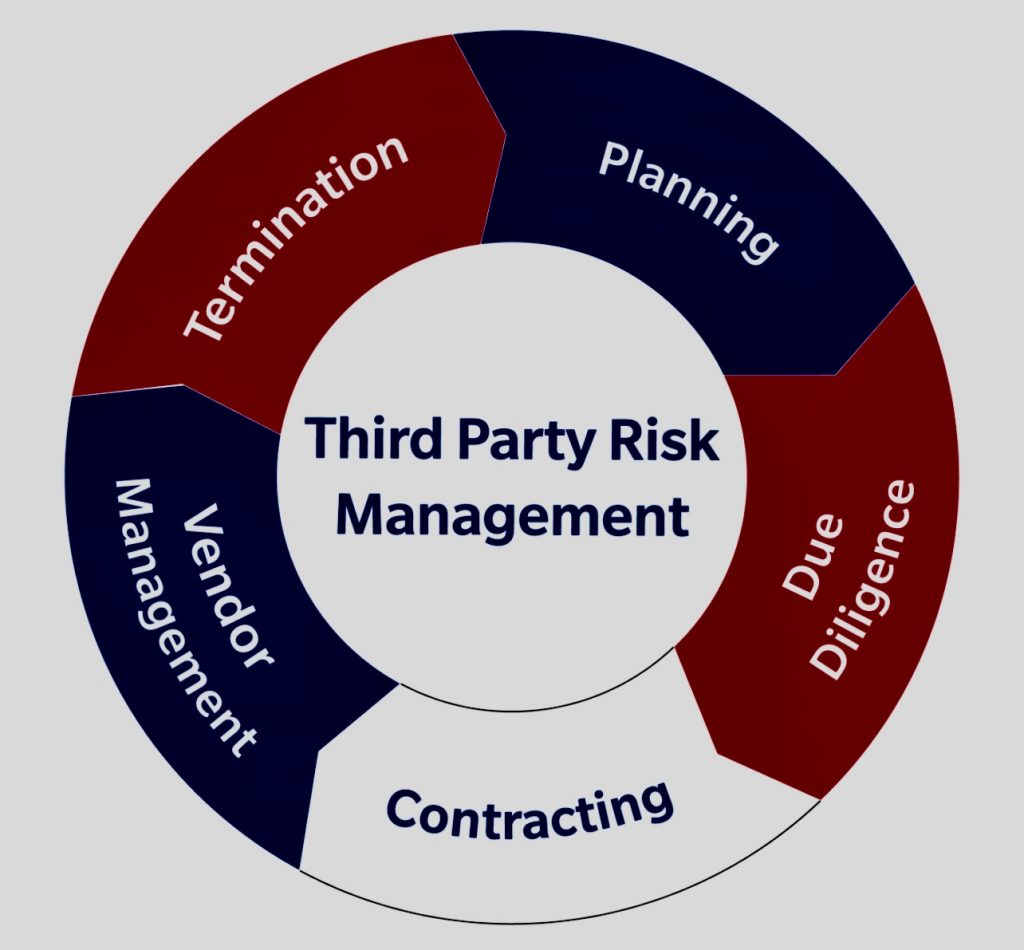
To effectively navigate these hidden risks, organizations need to adopt a proactive and comprehensive approach to third-party vendor management. This involves identifying, assessing, and mitigating risks throughout the vendor lifecycle, from onboarding to offboarding.
i. Identifying Third-Party Vendor Risks
The first step in navigating hidden risks is to identify the potential risks associated with each vendor. This requires a thorough understanding of the vendor’s business, the services they provide, and their access to the organization’s data and systems.
Key areas of focus for risk identification include:
A. Security and Privacy: Assess the vendor’s security practices, data handling procedures, and compliance with relevant regulations to safeguard sensitive information.
B. Financial Stability: Evaluate the vendor’s financial health and ability to meet contractual obligations to minimize disruptions to business operations.
C. Operational Resilience: Assess the vendor’s ability to maintain service continuity in the event of disruptions or outages to ensure business continuity.
D. Reputational Risks: Evaluate the vendor’s reputation; which could impact the organization’s image.
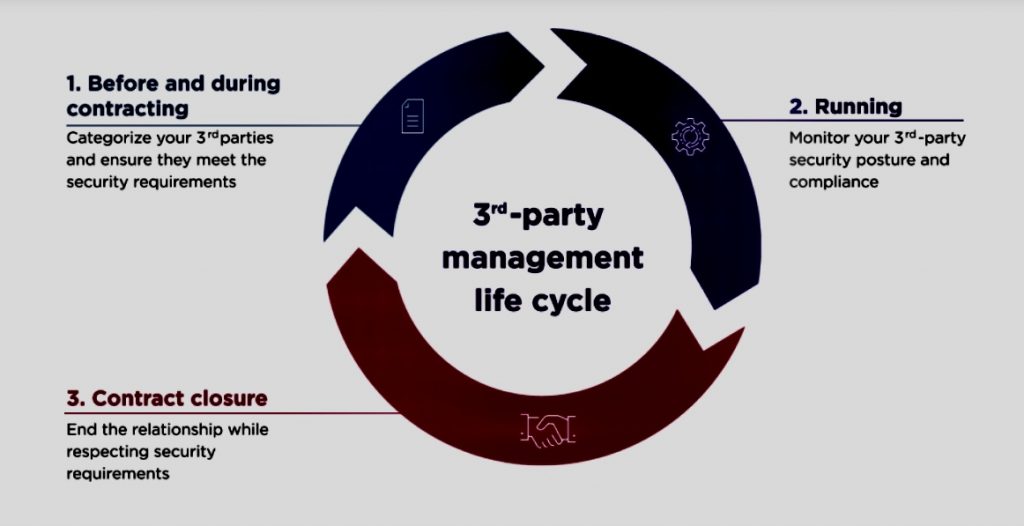
ii. Assessing Third-Party Vendor Risks
Once potential risks have been identified, a comprehensive assessment should be conducted to determine the likelihood and impact of each risk.
This involves using a range of risk assessment methodologies, such as qualitative and quantitative analysis, to prioritize risks based on their severity.
Here are key strategies to manage these risks effectively:
A. Comprehensive Vendor Assessment: Conduct thorough assessments before engaging with vendors. Evaluate their security practices, data protection measures, financial stability, and overall risk posture. Consider using standardized questionnaires and on-site visits for a deeper understanding.
B. Due Diligence in Vendor Selection: Prioritize vendors with a proven track record of security and reliability. Consider their reputation in the industry and gather references from other organizations that have used their services.
C. Regulatory Compliance Verification: Ensure that vendors comply with relevant regulations and industry standards. This is crucial, especially if they handle sensitive data or provide services in highly regulated sectors.
D. Contractual Agreements: Clearly define expectations and responsibilities in contractual agreements. Include specific clauses related to data protection, security measures, incident response, and the right to audit the vendor’s security practices.
E. Continuous Monitoring and Auditing: Implement ongoing monitoring of vendor activities and conduct periodic security audits. Regularly assess their compliance with contractual agreements and evaluate their security posture over time.
F. Data Handling and Storage Practices: Understand how vendors handle and store data. Ensure they follow best practices for data encryption, access controls, and data retention policies to prevent unauthorized access and data breaches.
G. Cybersecurity Insurance: Consider requiring vendors to maintain cybersecurity insurance coverage. This can provide an additional layer of protection in case of a security incident that impacts your organization.
H. Third-party Liability Insurance: Having third-party liability insurance can provide a layer of protection against potential vendor-related losses.
I. Vendor Access Controls: Implement strict access controls to limit vendor access to sensitive data and systems, and regularly review and update access permissions.
J. Incident Response Planning: Collaborate with vendors to develop incident response plans. Ensure that they have clear procedures in place to address and report security incidents promptly. Coordinate your response strategies to effectively manage joint incidents.
K. Supply Chain Visibility: Gain visibility into your vendor’s supply chain. Understand the potential risks associated with their subcontractors and assess whether they have mechanisms in place to manage and monitor their own third-party relationships.
L. Crisis Communication Protocols: Establish clear communication protocols for handling security incidents. Define how information will be shared, and ensure that both parties are aligned on communication strategies to maintain transparency during crises.
M. Employee Training for Vendors: Encourage vendors to invest in cybersecurity training for their employees. The human factor is a significant element in security, and well-trained vendor personnel contribute to overall risk mitigation.
N. Vendor Off-boarding: Establish a clear and structured off-boarding process to ensure the secure termination of vendor relationships, including data deletion, access revocation, and audit trails.
O. Exit Strategies: Develop exit strategies in case of terminating relationships with vendors. Ensure that data is securely transferred or deleted, and assess the potential impact on your organization’s operations during the transition.
P. Redundancy and Contingency Planning: Consider redundancy and contingency plans for critical services provided by vendors. Evaluate alternatives in case a vendor faces disruptions or is unable to deliver services temporarily.
Q. Benchmarking and Industry Comparisons: Continuously benchmark vendors against industry standards and compare their security practices with similar service providers. This ongoing assessment helps you stay informed about evolving best practices.
R. Collaboration with Peers: Collaborate with other organizations in your industry to share insights and experiences with specific vendors. Collective knowledge can provide valuable perspectives on potential risks and challenges associated with shared vendors.
S. Information Security and Compliance: Ensure vendors comply with data privacy, security standards, and other regulations prevalent in your industry. Regular audits can confirm a vendor’s systems, policies, and procedures are compliant.
T. Continuity Planning: It’s important to have a plan for switching to a new vendor or bringing services in-house if a vendor fails to deliver.
U. Vendor Risk Assessment: Regular assessment of vendor risks is fundamental. This might involve analyzing their financial stability, understanding the geopolitical context they operate within, their cybersecurity measures, and their disaster recovery plans.
V. Continuous Communication: The best way to avoid misunderstanding and miscommunication is by having regular discussions and updates. Open communication can prevent issues from becoming major problems.
W. Training: Train your employees to understand the risks involved in dealing with third-party vendors, and how to appropriately manage these.
X. Confidentiality Agreements and NDAs: To protect sensitive business information, have third-party vendors sign non-disclosure agreements (NDAs) or confidentiality agreements.
By adopting a proactive and comprehensive approach to third-party vendor management, organizations can effectively identify, assess, and mitigate the hidden risks associated with external partners, protecting their valuable data, maintaining business continuity, and safeguarding their reputation.
https://telefonicatech.com/en/blog/third-party-risk-the-hidden-threat-to-your-business
