Building Cyber Resilience: Vital Strategies for Your Business
In today’s digital landscape, where businesses rely heavily on technology, the importance of cybersecurity cannot be overstated. Cyber threats are ever-evolving, and organizations must prioritize building cyber resilience to withstand and recover from potential attacks.
i. Preventative Measures:

A. Strengthen your defenses: Implement the “Essential Eight” security controls from the Australian Cyber Security Centre. These include antivirus, firewalls, patching applications, multi-factor authentication, restricting admin privileges, and regular backups.
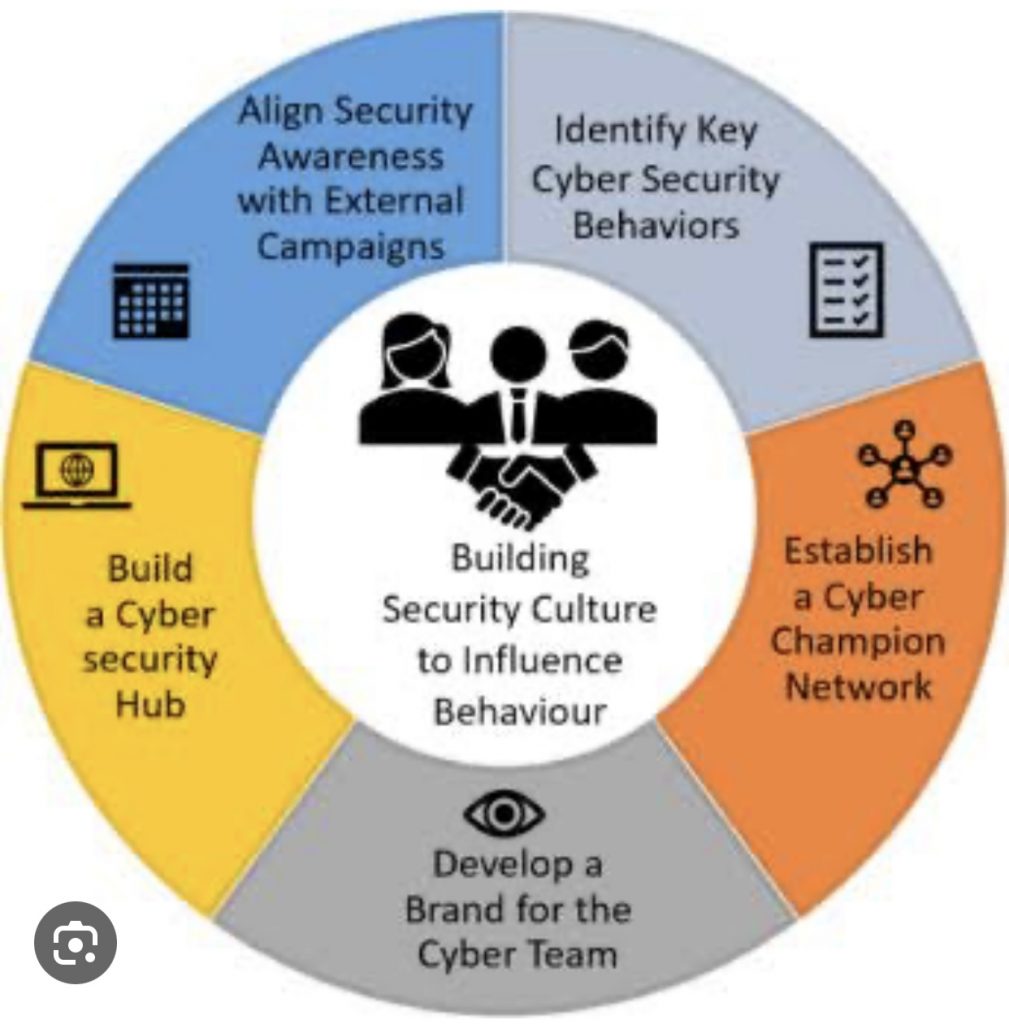
B. Employee awareness: Train your staff on common cyber threats like phishing and social engineering. Regular training and simulations can help build a security-conscious culture.
C. Access control: Limit access to sensitive data based on the principle of least privilege. Regularly review and update access permissions.
D. Data security: Encrypt sensitive data both in transit and at rest. Consider data loss prevention tools to monitor and control data movement.
E. Software updates: Update software and operating systems promptly to patch vulnerabilities exploited by attackers.
ii. Proactive Measures:
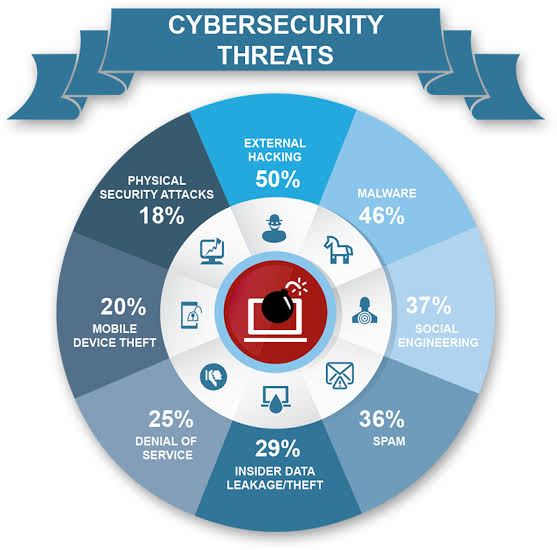
A. Risk assessment: Conduct regular risk assessments to identify and prioritize potential vulnerabilities. Develop mitigation plans for identified risks.
B. Penetration testing: Simulate cyberattacks to uncover vulnerabilities in your systems before real hackers do.
C. Incident response plan: Develop a plan for responding to cyberattacks, including communication protocols, containment strategies, and recovery procedures.
D. Business continuity plan: Ensure your business can continue operating even if a cyberattack disrupts core functions. Regularly test and update your plan.
iii. Key strategies to incorporate cyber resilience into your business:

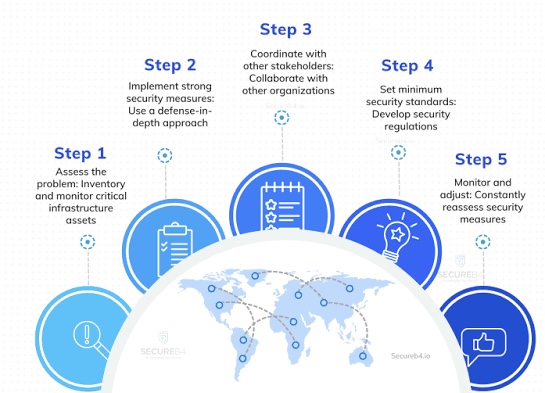
A. Risk Assessment: Identify your critical assets, the threats to those assets, and your vulnerabilities. Assessing the risks helps you prioritize where to focus your cyber resilience efforts.
B. Incident Response Planning: Develop and implement an incident response plan that outlines what to do before, during, and after a cyber incident. Regularly update and test this plan through exercises and drills.
C. Business Continuity Strategies: Ensure you have a robust business continuity plan that includes how to maintain operations during and after an attack, reducing downtime and economic impact.
D. Training and Awareness: Conduct regular training sessions for all employees on cyber threats and best practices to mitigate them. Establishing a culture of security awareness is crucial for cyber resilience.
E. Redundant Systems: Implement redundant data storage and processing systems to ensure that critical functions can remain online even if one system is compromised.

F. Develop a Cyber Resilience Plan: Outline procedures and steps to be taken before, during, and after a cyber attack. This will help minimize disruption to your business operations and lessen the impact of a cyber threat.
G. Employ Threat Intelligence: This pertains to staying informed about the latest cyber threats and vulnerabilities in your industry or area. Rapid response to newly discovered threats is vital for effective cyber resilience.
H. Disaster Recovery and Business Continuity Plan: Have a plan to resume operations as quickly as possible after a cyber attack. This involves having a recovery system in place, with vital data and operations being restored first.
I. Invest in Resilient Technologies: Utilize cybersecurity technologies designed to adapt and learn from new threats, such as those with machine learning capabilities.
J. Invest in Cybersecurity Technologies: Use firewalls, anti-virus software, and encryption for data protection. Also consider advanced tools like intrusion detection systems and data loss prevention tools.
K. Strong Access Controls: Employ robust access controls such as multi-factor authentication, ensuring only authorized users have access to sensitive data and systems.
L. Secure Configurations: Ensure that all devices and systems are configured securely. This includes applying the principle of least privilege, where users and systems have only the minimum access required for their roles, reducing the attack surface.
M. Regular Updates and Patch Management: Regularly update and patch your systems and software to fend off known vulnerabilities.
N. Cybersecurity Audits and Risk Assessments: Conduct regular cybersecurity audits and risk assessments to identify potential weaknesses in your systems. This proactive approach allows you to address vulnerabilities before they can be exploited, bolstering your organization’s overall resilience.
O. Collaboration and Sharing: Engage in knowledge sharing about threats and best practices with other businesses and cybersecurity organizations.
P. Third-Party Risk Management: Assess the cybersecurity measures of your business partners, suppliers and vendors. Ensure they follow good cybersecurity practices, as they can become a potential weak link in your security.
Q. Multi-Factor Authentication: Implement multi-factor authentication where sensitive data is involved. This adds an additional layer of security, making it more difficult for cyber criminals to access your systems.
R. Insurance: Invest in cybersecurity insurance to mitigate financial losses in the event of a cyber incident.
S. Adaptive Defense Strategies: Implement security measures that are not only preventive but also adaptive, continually evolving as potential threat scenarios change.
T. Cyber Resilience Metrics: Define and monitor key performance indicators (KPIs) related to cyber resilience to measure your organization’s performance over time.
U. Continuous Monitoring and Anomaly Detection: Implement robust monitoring tools to keep a close eye on network traffic. Detecting unusual activities or anomalies early can help identify potential threats before they escalate, enabling a proactive response.
Incorporating cyber resilience into your business involves a layered, strategic approach to not just protect against potential cyber threats but also to ensure that your business can continue to operate effectively in the event of a breach or attack.
https://www.weforum.org/agenda/2022/07/4-ways-to-incorporate-cyber-resilience-in-your-business/
https://resiliencefirst.org/news/improving-cyber-resilience-your-business
https://www.cio.com/article/648180/turning-cyber-risk-into-business-resilience.html?amp=1