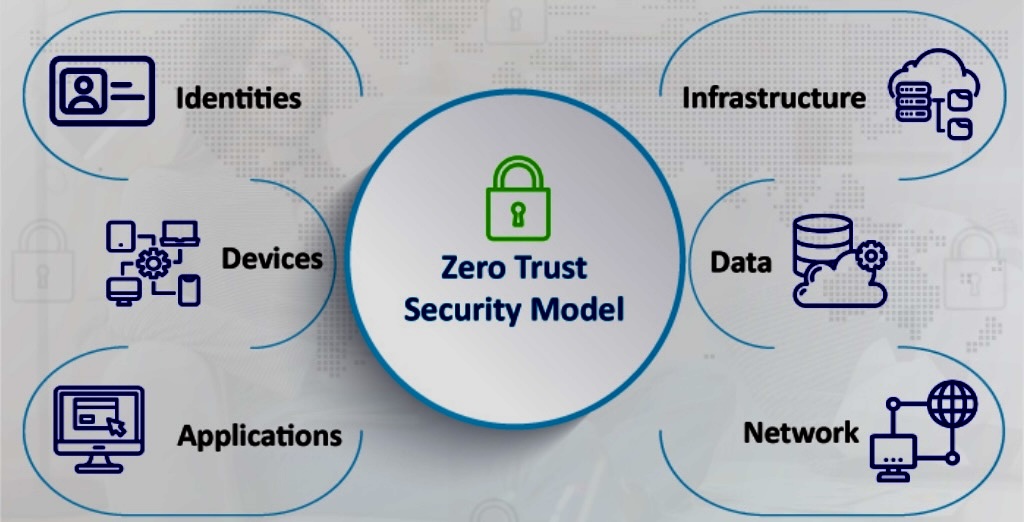
Zero Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access.
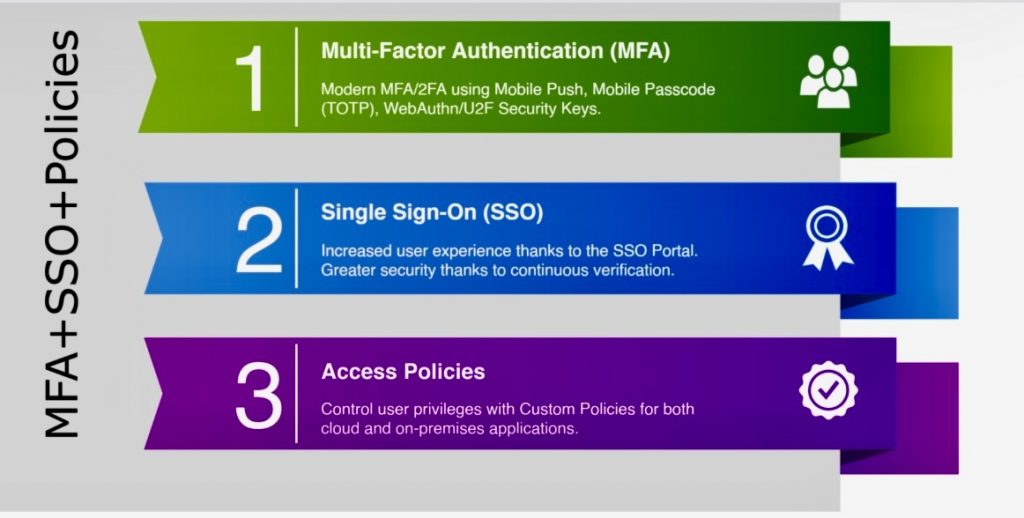
How Zero Trust can help in reducing the cost of security:
A. Definition of Zero Trust:
o Principle: Zero Trust is a cybersecurity framework that operates on the assumption that organizations should not automatically trust anything, inside or outside their network perimeter. Every user, device, and application is treated as untrusted, requiring continuous verification.
B. Traditional Security Challenges:
o Perimeter Reliance: Traditional security models rely heavily on perimeter defenses, assuming that once inside, entities can be trusted. This approach becomes insufficient in the face of sophisticated cyber threats.
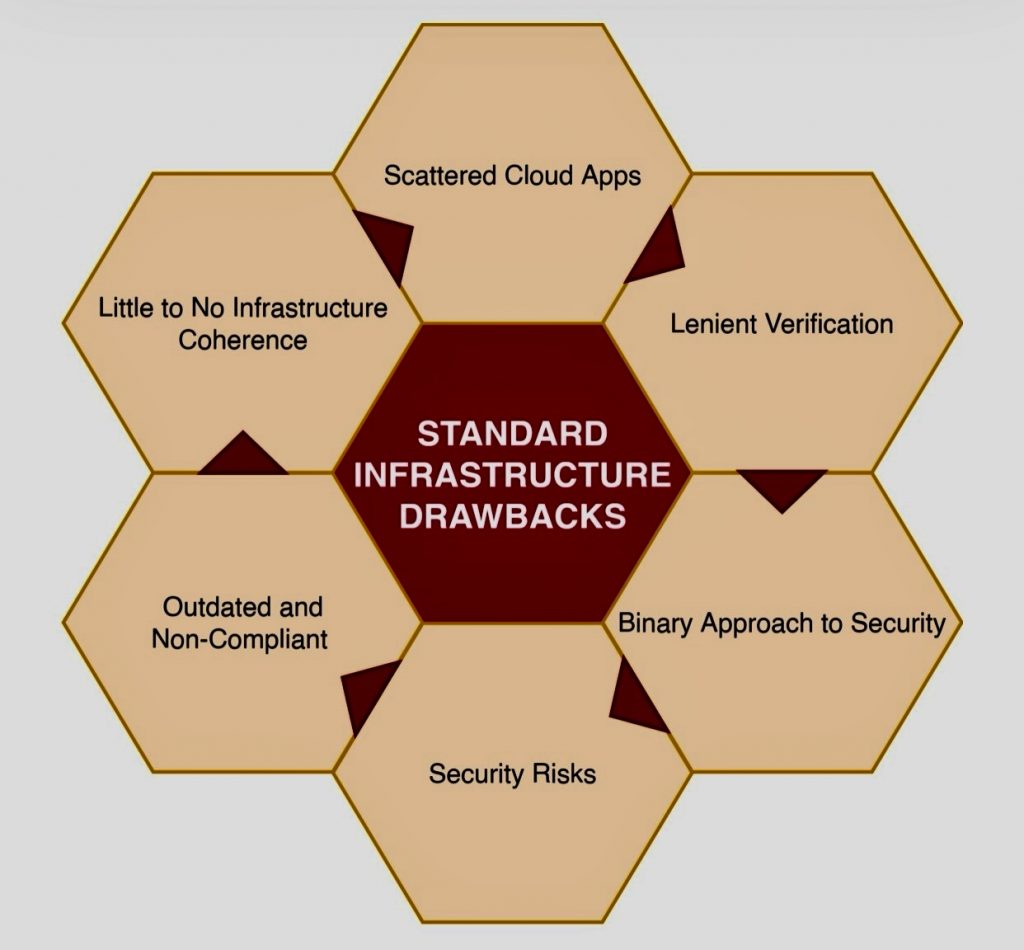
C. Key Principles of Zero Trust:
o Verify Identity: Continuously verify the identity of users, devices, and applications.
o Least Privilege: Grant the minimum level of access required for users and systems to perform their tasks.
o Micro-Segmentation: Segment the network into small, isolated zones to contain and minimize the impact of potential breaches.
o Continuous Monitoring: Implement continuous monitoring and analysis of network activities for anomalies.
D. Reduced Risk of Data Breaches: Zero trust can help to reduce the risk of data breaches by preventing unauthorized access to sensitive data. This can save organizations millions of dollars in potential costs associated with data breaches, such as fines, legal fees, and remediation costs.
E. Reduced Attack Surface: By enforcing least-privilege access, Zero Trust minimizes the attack surface, and hence the potential for intrusions. Fewer attacks mean less money needing to be spent on threat hunting, incident response, and remediation efforts.
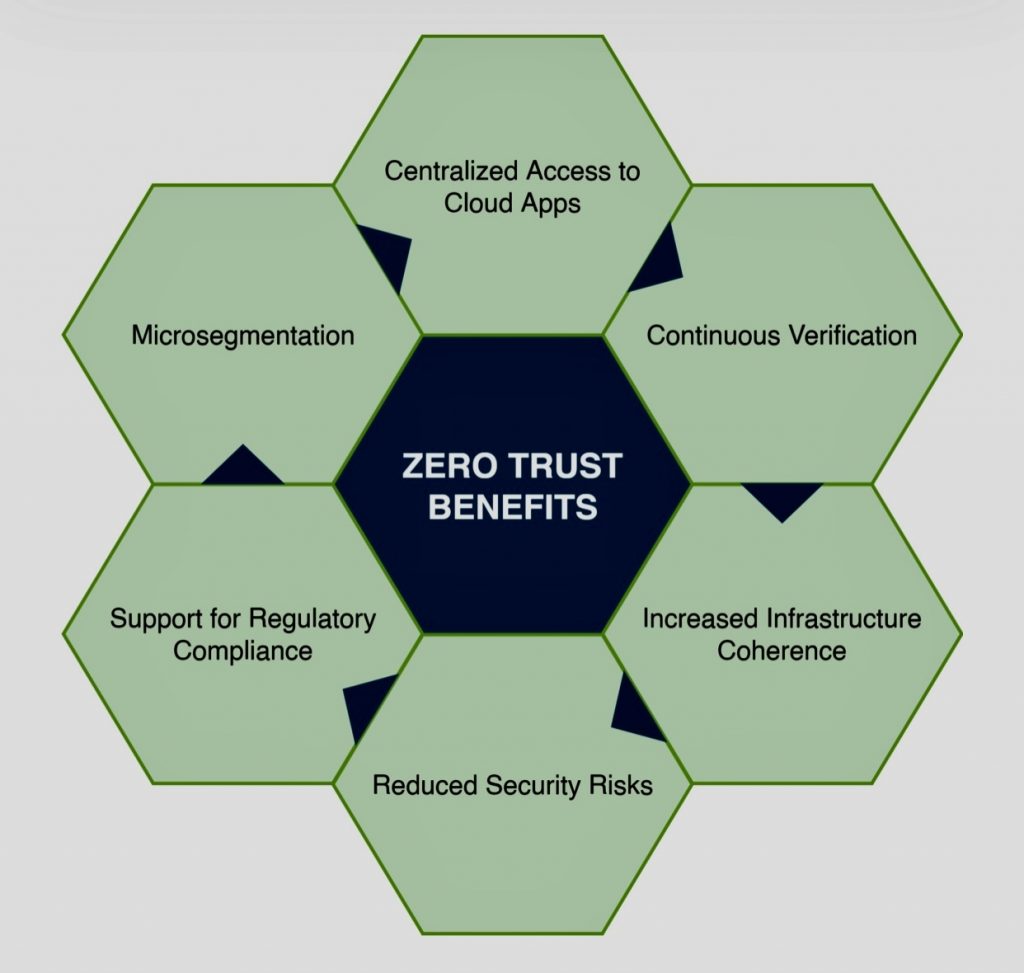
F. Improved Compliance: Zero trust can help organizations to comply with data privacy regulations, such as GDPR and CCPA. This can reduce the risk of fines and other penalties for non-compliance.
G. Rationalization of Tools: Implementing a Zero Trust architecture often forces organizations to rationalize the security tools they use, which can lead to cost savings by eliminating redundant or underutilized solutions.
H. Automation: Zero Trust can lead to greater levels of security automation, as consistent policies are easier to automate. Automation can subsequently lead to lower labor costs and fewer human errors.
I. Flexible Work Arrangements: Zero Trust allows employees to securely access business systems and data from any location or device, reducing the need for costly on-site IT infrastructure.
J. Proactive Approach: Instead of a reactive stance where organizations respond to incidents after they occur, Zero Trust takes a proactive approach by consistently verifying every user and every action, potentially stopping attacks before they happen.
K. Enhanced Productivity: Zero trust can help to increase employee productivity by reducing downtime caused by security incidents. This can save organizations millions of dollars in lost productivity each year.
L. Improved Reputation: Zero trust can help to improve an organization’s reputation by demonstrating its commitment to data security. This can attract new customers and partners and retain existing ones.
M. Cost Reduction through Zero Trust:
o Minimized Data Exposure: Zero Trust helps minimize data exposure by enforcing least privilege. This reduces the potential impact of a data breach and associated cleanup costs.
o Prevention of Lateral Movement: By segmenting the network and requiring continuous verification, Zero Trust limits the ability of attackers to move laterally within the network, preventing the spread of a compromise.
o Reduced Incident Response Costs: With continuous monitoring and early detection, Zero Trust facilitates quicker incident response, minimizing the financial impact of security incidents.
o Savings on Compliance Penalties: Zero Trust aids in maintaining compliance by enforcing strict access controls and data protection measures, reducing the risk of regulatory fines.

N. Implementation Steps:
o Identify and Classify Assets: Identify and classify assets, determining their criticality and sensitivity.
o Implement Least Privilege: Enforce the principle of least privilege, ensuring users and systems have only the necessary access.
o Continuous Monitoring: Invest in tools and processes for continuous monitoring of network activities, detecting anomalies promptly.
o Micro-Segmentation: Implement micro-segmentation to compartmentalize the network and limit lateral movement.
o User and Device Authentication: Strengthen user and device authentication mechanisms, including multi-factor authentication.
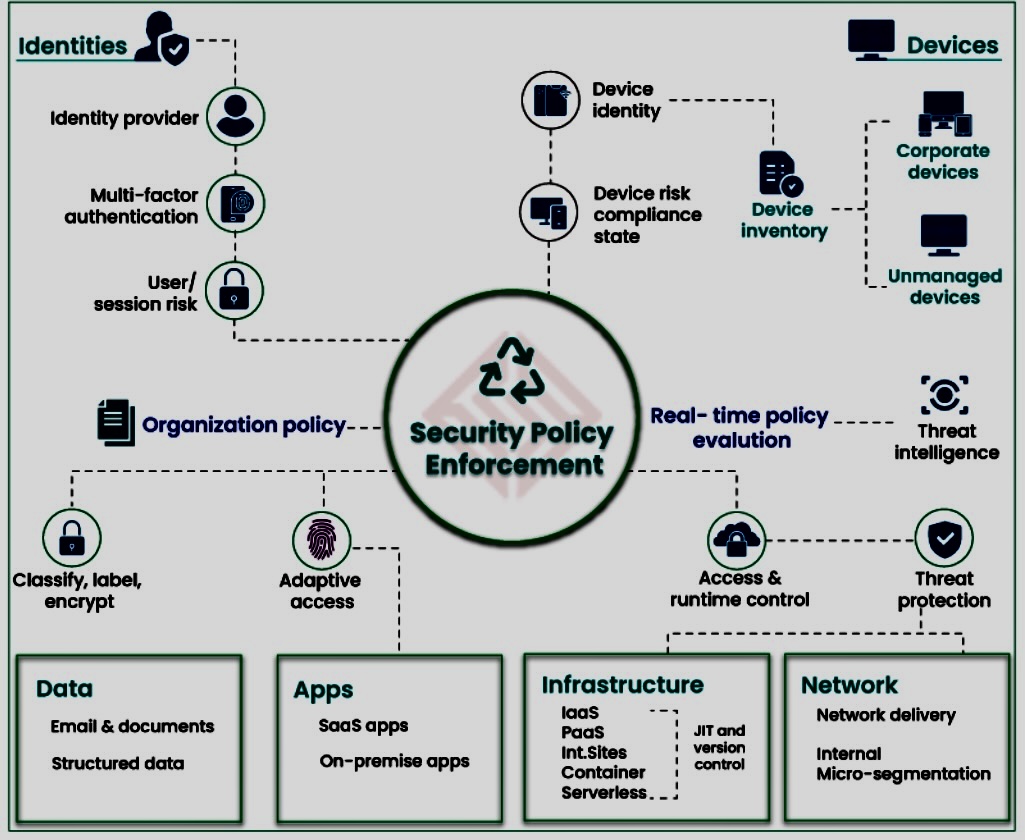
O. Technology Enablers:
o Zero Trust Access (ZTA): Utilize Zero Trust Access solutions that enable secure access to applications and data based on the principle of continuous verification.
o Software-Defined Perimeter (SDP): Implement SDP to dynamically create secure perimeters around specific applications or data, reducing the attack surface.
Q. Collaboration and User Education:
o Employee Training: Educate employees about the principles of Zero Trust, emphasizing their role in maintaining a secure environment.
o Collaboration with Vendors: Work collaboratively with third-party vendors and partners to extend Zero Trust principles to external entities.
R. Regular Audits and Assessments:
o Periodic Assessments: Conduct regular assessments and audits to ensure that Zero Trust policies are effectively implemented and aligned with evolving security requirements.
S. Adaptation to Evolving Threats:
o Continuous Improvement: Continuously adapt Zero Trust measures to address new and evolving cyber threats. Regularly review and update security controls.
T. Improve incident response: Zero trust can help organizations to respond to security incidents more quickly and effectively.
U. Business Continuity and Resilience:
o Enhanced Resilience: Zero Trust enhances business resilience by minimizing the impact of security incidents and enabling swift recovery.
Although there may be upfront costs associated with switching to a Zero Trust model, the long-term cost-saving benefits often outweigh these initial investments.
By prioritizing continuous verification, least privilege access, and effective segmentation, organizations can strengthen their defenses and minimize the financial and operational impact of security incidents.
https://www.crowdstrike.com/cybersecurity-101/zero-trust-security/
https://www.linkedin.com/pulse/benefits-zero-trust-security-businesses-primetel-communications
