Ways Security Can Cost Your Business
Do you know how secure your organization is—and what the costs of a data breach can be?
If you’re like most organizations, you probably have a pretty good sense of the potential fallout, particularly in light of recent, high-profile breaches. It’s no wonder that 64% of security decision makers say that adopting a data-centric approach to security is a high priority over the next 12 months.
The fact is, data breaches are growing in number, and the financial cost is growing too. The average cost of a data breach has nearly doubled in the past five years, from $6.46 million in 2010 to $12.9 million today.
But the costs aren’t just monetary. What about damage to your reputation? Customers and users place an enormous amount of trust in the companies with whom they do business. A single breach can damage that trust forever. What about intellectual property that if leaked, could sound the death knell for any organization? There’s no recovery.
Today, security isn’t just about basic monitoring services. Companies have far more to consider than they once did, particularly when you consider the rise of new technologies and business usage scenarios, like Cloud and BYOD. Instead, it’s a holistic approach to protection, prevention, and response—and it needs to encompass all aspects of technology.
Here’s what you need to consider when implementing, updating, and enforcing your security policy. Some of the items might surprise you.
“Many organizations, despite having implemented some of the more standard countermeasures (i.e., firewalls, antivirus, IDs) still do not have visibility across their environment to understand what is happening at any given time.” — IDC
External Threats
Welcome to the digital age: the sheer number of external threats is growing, and there’s absolutely nothing that we can do about it—other than maintaining constant vigilance through a security policy that is constantly updated and enforced.
The speed at which threats are increasing is exponential. For instance, there are millions of malware variations that enterprises must defend against, but it’s difficult for signature-based malware to keep up. There are more distributed denial-of-services (DDoS) attacks than ever before, and they vary widely; they can be highly targeted or generic, long in duration or short. And they mutate; there’s a new breed of DDoS attacks that use Web servers as payload carrying bots, which makes them even more deadly because of exponential performance increases. And then there are application attacks—25% of all DDoS attacks—which are often targeted at financial systems, which can bring a company to its knees.
What’s even more problematic is that most organizations have already been breached—they just don’t know about it. Malicious operators are like sharks constantly nibbling at the cage. They’re always there. They’re often already inside. And it can be just a matter of time before they strike.
100% of business networks analyzed by Cisco have traffic going to websites that host malware
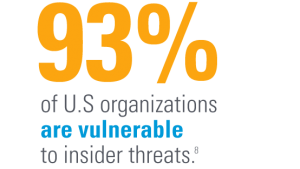
Internal Threats
External threats are real and dangerous. But internal threats can be just as common—and just as damaging. And we’re not just talking about the disgruntled employee who leaks sensitive data right after they’re fired, although this is a phenomenon that does exist (often with dire consequences).
Instead, internal threats are often inadvertent, stemming from a lack of oversight. Ask yourself the following:
• Do your employees download whatever software they want on their work computers?
• Can people access sensitive corporate data on their personal devices?
• Do workers conduct business using their smart phones?
In other words—does your organization have policies for what employees can do with company information, how they can access it, and what applications they can download? And is managing BYOD scenarios a key part of that policy?
If the answer is no, you have a security problem. More likely, you do have a security policy in place—but if you’re not enforcing them, it’s as good as not having one at all. If this is you, you’re not alone. According to a recent survey by DataMotion, 44% of respondents only moderately enforce their internal security policies.
But internal threats are just as real as external threats—and companies that don’t get a handle on them are at risk.
Untrained Staff
When it comes to security, one key oversight is not training people. It’s imperative that employees know what your security policies are—all the way from what devices they can use to what applications they can download. Educate. Evangelize. Enforce. Let them know.
The rising problem of Shadow IT
More and more organizations are struggling with Shadow IT, the use of hardware or software that is not supported or authorized by an organization’s IT department. Shadow IT can range from developers using various Software-as-a-Service platforms to employees storing corporate data in cloud storage solutions like Dropbox or Google Drive. These solutions seem innocuous to most people—which is why employees need to receive comprehensive training about what is a security risk and what isn’t.
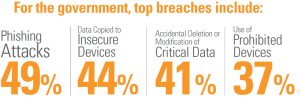
53% of federal government IT security decision makers state that careless and untrained insiders pose the greatest IT security threat to their agencies.
Governmental Compliance
Would you pass an audit for governmental compliance with security policies?
The surprising news is that a large number of companies aren’t sure they would. In fact, a survey demonstrated that nearly 60% of 7809 IT and business-decision makers in North America are only moderately confident that their organizations would be compliant with requirements for protecting across a wide variety of industries.10 Even more shocking? Global PCI compliance is only at 20%.
Complicating matters is the fact that many organizations don’t even know that governmental compliance regulations apply to them.
Take healthcare for instance. There are many companies that work downstream from healthcare organizations. If they’re handling Protected Health Information, they must be HIPAA-compliant. The law handles this by requiring that the hiring healthcare organization have them sign paperwork stating that they are a Business Associate. Yet according to a DataMotion survey, 40.5% of respondents had either not been asked to sign a Business Associate agreement, or weren’t sure if they had signed one.
Both the Business Associate and the healthcare organization are at risk for non-compliance.
But even more worrisome? How simple it is for confidential patient healthcare information to be compromised when a company is not compliant.
Choosing the Right Partners
More and more organizations are choosing to outsource their security operations—no surprise given the fact that IT outsourcing is a growing trend in and of itself. But when it comes to outsourcing security, it’s truly buyer beware. The first step? You need to understand exactly what it is that you need to protect—generally, devices, network, applications, and data—and then determine what components of these you’re outsourcing. The second step is to choose the right partner or partners for your specific needs. And keep in mind that the more you can consolidate vendors, the more efficient your strategy will be.
Balancing performance and cost
Make no mistake: security is expensive. Not having security is even more expensive. But part of choosing the right partner comes down to understanding the balance between performance and cost. The simple fact is that you will never be 100% secure. Choose a vendor who can help you make the right decisions around balancing performance, effectiveness, and cost.
Physical Security
Physical security is the protection of people, hardware, programs, networks, and data from any damage that might occur. In other words, it’s having a data center that is protected from fire, natural disasters, burglary, terrorism, theft … the list goes on and on. If your physical system isn’t secure, nothing else matters. Yet physical security is one of the most overlooked aspects of a security strategy.
The physical management of data centers includes all aspects of the physical security, including security policies and procedures, security officer staffing, access control systems, video surveillance systems, standards compliance, and physical security designs and improvements within the data centers. Make sure the data center you choose complies with standards—and that you get annual audits.