Enhancing cybersecurity culture within an organization is crucial for safeguarding sensitive data, protecting systems, and mitigating cyber threats. A strong cybersecurity culture fosters a mindset of vigilance, responsibility, and proactive measures to address potential vulnerabilities.
Here are some key ways to improve cybersecurity culture:
A. Leadership Commitment and Support:
a. Senior management should demonstrate unwavering commitment to cybersecurity, setting the tone for the organization’s approach.
b. Cybersecurity should be embedded into the organization’s overall strategy, aligning with business objectives and risk management practices.
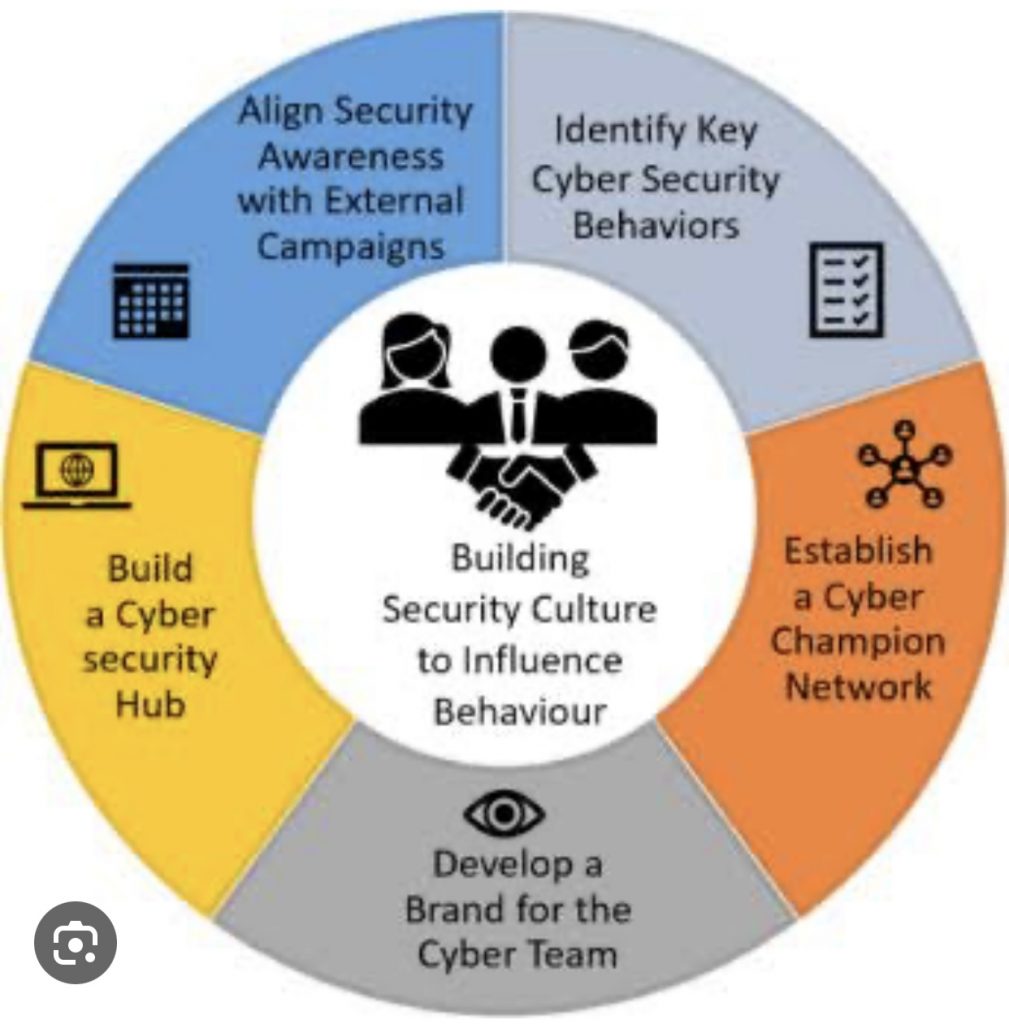
c. Cybersecurity should be Integrated into the organization’s values and priorities.
d. Leadership should allocate sufficient resources, including funding, personnel, and technology, to support cybersecurity initiatives.
e. Lead by example to set the tone for a security-conscious culture.
B. Clear Policies and Procedures:
a. Establish clear and concise cybersecurity policies and procedures.
b. Ensure that employees understand and adhere to these policies, covering areas such as password management, data handling, and acceptable technology usage.
C. Create a Cybersecurity Policy: Develop a strong, clear, and executable cybersecurity policy that provides a roadmap of actions to take to safeguard your organization’s digital information. This should include steps like proper data storage and management, secure account management, incident response plans, etc.
D. Education and Awareness:
a. Provide comprehensive cybersecurity training to all employees, covering topics such as password management, phishing scams, social engineering attacks, and data protection.
b. Regularly conduct cybersecurity awareness campaigns to reinforce best practices and educate employees on emerging threats.
c. Encourage open communication and feedback from employees to address concerns and misconceptions about cybersecurity.
d. Make training engaging, relevant, and tailored to different roles within the organization.
E. Continuous Learning:
a. Foster a culture of continuous learning by staying updated on emerging cybersecurity threats and trends.
b. Offer ongoing training and resources to keep employees informed about the evolving landscape.
F. Security Awareness Campaigns:
a. Launch targeted awareness campaigns to coincide with cybersecurity awareness months or relevant events.
b. Use creative and engaging methods to convey key security messages.
G. Promote Strong Password Hygiene: Encourage the use of strong, unique passwords and the use of a password manager if necessary. Also, implement multi-factor authentication where possible.
H. Encourage Reporting: Encourage employees to report any suspicious activity, unusual network behavior or phishing attempts. This can help you tackle threats swiftly.
I. Practice Safe Browsing: Employees should always verify the security of the websites they visit to reduce the risk of phishing or malware attacks.
J. Social Engineering Awareness: Many cyber attacks start with social engineering. Teach employees about the various forms, such as email impersonation and deceptive links, and how to identify and report them.
K. Vulnerability Management and Patching:
a. Implement a robust vulnerability management program to identify and prioritize security flaws in systems and applications.
b. Proactively apply security patches and updates to address known vulnerabilities, reducing the risk of exploitable loopholes.
c. Utilize automated vulnerability scanning tools and integrated patching solutions to streamline the process.
L. Simulate Cyber attacks: Regular drills can help employees get real-time practice of how to detect and respond to cyber threats.
M. Regular Updates and Patches: Keep all systems, software and devices updated and patched. This helps protect from vulnerabilities that hackers could exploit.
N. Access Control and Privilege Management:
a. Implement strict access control policies to restrict access to sensitive data and systems based on individual roles and responsibilities.
b. Enforce least privilege principles, granting users only the access they need to perform their job functions.
c. Enforce the principle of least privilege, ensuring employees have access only to the information and systems necessary for their roles.
d. Regularly review and audit user access permissions to identify and remediate unauthorized access or excessive privileges.
O. Implement Role-based Access Control (RBAC): Only necessary powers and access levels should be provided to employees based on their job roles to reduce the risk of internal threats and data breaches.
P. Data Protection and Data Loss Prevention (DLP):
a. Implement data classification and labeling policies to categorize sensitive data based on its value and sensitivity.
b. Employ data loss prevention (DLP) solutions to monitor and control data exfiltration, preventing unauthorized data transfers and disclosures.
c. Regularly review and update data handling procedures to ensure compliance with data protection regulations and industry standards.
Q. Incident Response and Reporting:
a. Establish a comprehensive incident response plan that outlines procedures for identifying, containing, and eradicating cyber attacks.
b. Designate a team of cybersecurity experts to respond to security incidents effectively and efficiently.
c. Encourage employees to report suspicious activities or potential breaches promptly to facilitate timely investigation and remediation.
d. Conduct regular drills and simulations to ensure employees are familiar with the procedures to follow in the event of a cybersecurity incident.
R. Regular Penetration Testing and Vulnerability Assessments:
a. Conduct regular penetration testing and vulnerability assessments to identify and assess potential security weaknesses in systems and networks.
b. Leverage the findings from penetration tests and vulnerability assessments to prioritize and address security gaps.
c. Continuously monitor and update security controls to maintain a proactive approach to cybersecurity.
S. Third-Party Risk Management:
a. Implement due diligence processes for evaluating and onboarding third-party vendors and service providers to ensure they meet acceptable security standards.
b. Monitor and audit the security practices of third-party vendors to maintain ongoing assurance of their compliance and effectiveness.
c. Include cybersecurity clauses in contracts with third-party vendors to establish clear responsibilities and expectations for data protection.
T. Culture of Vigilance and Continuous Improvement:
a. Foster a culture of cybersecurity awareness and responsibility throughout the organization, encouraging employees to be vigilant and report suspicious activities.
b. Encourage continuous learning and improvement in cybersecurity practices, staying updated on emerging threats, vulnerabilities, and mitigation strategies.
c. Regularly review and update cybersecurity policies, procedures, and training programs to adapt to evolving risks and technologies.
U. Community Building:
a. Encourage a sense of community among employees by organizing cybersecurity-themed events, workshops, or forums.
b. Create a collaborative environment where employees can share insights and experiences.
V. Cybersecurity Champions: Establish a team of cybersecurity champions who take extra initiative in maintaining and promoting cybersecurity practices within the organization.
W. Regular Audits and Assessments:
a. Conduct regular cybersecurity audits and assessments to identify vulnerabilities.
b. Use findings to improve security controls and educate employees on areas that need attention.
X. Regular Communication:
a. Maintain open and transparent communication channels regarding cybersecurity matters.
b. Use multiple mediums, including emails, newsletters, and posters, to share updates, tips, and reminders.
Y. Employee Involvement:
a. Encourage employees to actively participate in maintaining a secure environment.
b. Establish channels for reporting security incidents, suspicious activities, or potential vulnerabilities.
Z. Secure Personal Devices: If employees use personal devices for work, those need to be secured as well. This can mean installing security software or regulating that company data can only be accessed through secure apps.
AA. Secure Remote Work Practices:
a. Provide guidelines and training for secure remote work practices, considering the increased prevalence of remote work.
b. Emphasize the importance of using virtual private networks (VPNs) and secure communication tools.
AB. User-Friendly Security Measures:
a. Implement security measures that are user-friendly to encourage compliance.
b. Strive to strike a balance between security and usability to avoid creating obstacles that might lead to circumvention.
AC. Recognition and Rewards:
a. Acknowledge and reward employees who contribute to the organization’s cybersecurity efforts.
b. Consider implementing recognition programs to highlight security champions.
AD. Use Of Advanced Technologies: Implement advanced security technologies such as AI, machine learning, and encryption to boost the cybersecurity measures of the organization.
Cybersecurity is a continuous process and needs constant attention and improvement.
Creating a cybersecurity culture is an ongoing process that necessitates an evolving strategy to keep up with the changing landscape of threats. It is a collaborative effort between the leadership, IT departments, and all other employees.
https://blog.securitymentor.com/tips-to-improve-your-organizations-security-culture
