
Embracing the Zero-Trust Model: A Paradigm Shift in Organizational Security
This realization has led to a strategic pivot towards the Zero Trust security model, a paradigm that operates on the principle of “never trust, always verify.”
But what drives organizations to adopt this model, and how does it represent a departure from conventional security practices?
i. The Evolving Threat Landscape
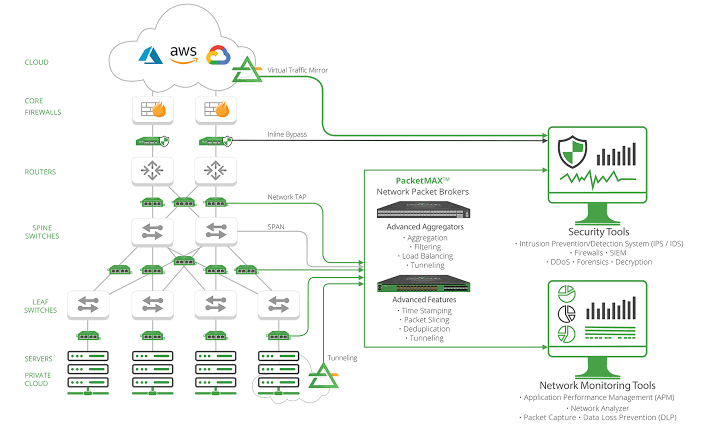
The digital transformation of businesses has expanded the attack surface exponentially. Cloud services, mobile devices, and the Internet of Things (IoT) have blurred the traditional boundaries of networks, rendering perimeter-based security models less effective. Cyber attackers today exploit these vulnerabilities, launching attacks that bypass perimeter defenses with relative ease. Moreover, the rise in remote work has further diluted the effectiveness of conventional security measures, highlighting the need for more robust and adaptable frameworks.
ii. Limitations of Conventional Security Models
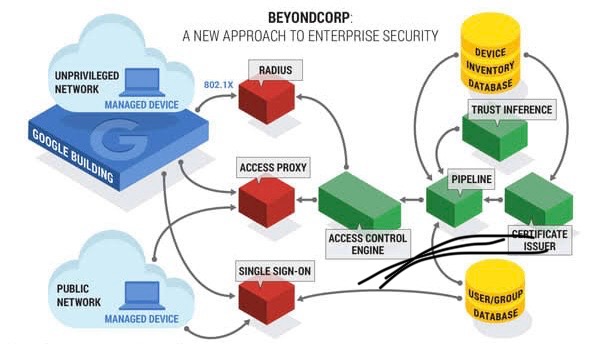
Traditional security models operate under the assumption that everything inside the network is trustworthy, focusing most of their resources on preventing external threats from breaching the network perimeter. However, this leaves organizations vulnerable to internal threats and to sophisticated attackers who can penetrate perimeter defenses. Once inside, these malicious actors can move laterally across the network with little impedance, accessing sensitive information and systems.
iii. The rise of remote work
The advent of remote work has expanded the perimeter beyond the physical office space, introducing new vulnerabilities. Employees accessing corporate resources from various locations, on different networks, often using personal devices, have made perimeter-based security models obsolete. The zero-trust model accommodates this modern workforce by securing access regardless of location, thereby ensuring consistent application of security policies.
iv. Cloud Adoption
As organizations migrate to cloud services, their data no longer resides solely within their immediate control but is distributed across various cloud environments. This transition necessitates a security model like zero trust, which secures data and applications irrespective of their location, by focusing on securing access rather than defending a perimeter that no longer exists.
v. Regulatory Compliance
Stricter regulatory requirements for data protection and privacy, such as GDPR, HIPAA, and CCPA, compel organizations to adopt a more thorough approach to security. The zero-trust model, with its premise of “never trust, always verify,” is inherently designed to minimize data breaches and ensure compliance by providing detailed insight and control over data access and usage.
vi. Enhanced Visibility and Control
Zero trust provides organizations with greater visibility into their network traffic and fine-grained control over access to their resources. By requiring constant verification, organizations can monitor who is accessing what data, from where, and on what device, allowing for a more detailed understanding of their security posture and enabling them to react quickly to potential threats.
vii. Digital Transformation and IoT
The digital transformation of businesses, coupled with the proliferation of IoT devices, has exponentially increased the number of connected devices on a network, each representing a potential entry point for attackers. The zero-trust model, by enforcing strict access controls and continuous monitoring of all devices, alleviates the security challenges associated with these connected ecosystems.
viii. Cost Efficiency
Contrary to the assumption that more comprehensive security solutions are inherently more costly, the zero-trust model can lead to cost savings in the long run. By preventing breaches more effectively, organizations save on the considerable costs associated with cyber incidents, including data recovery, legal fees, regulatory fines, and reputational damage.
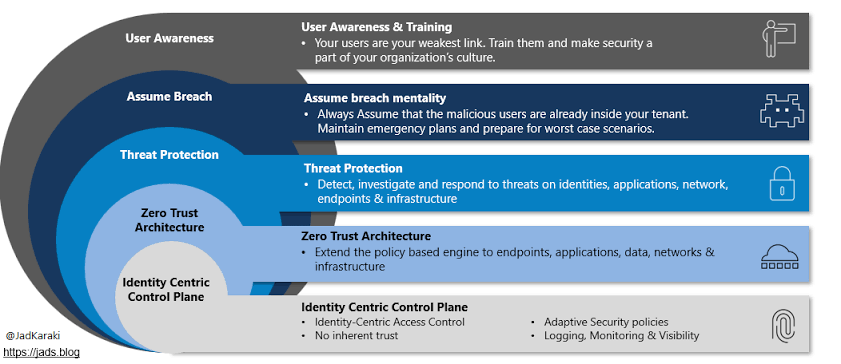
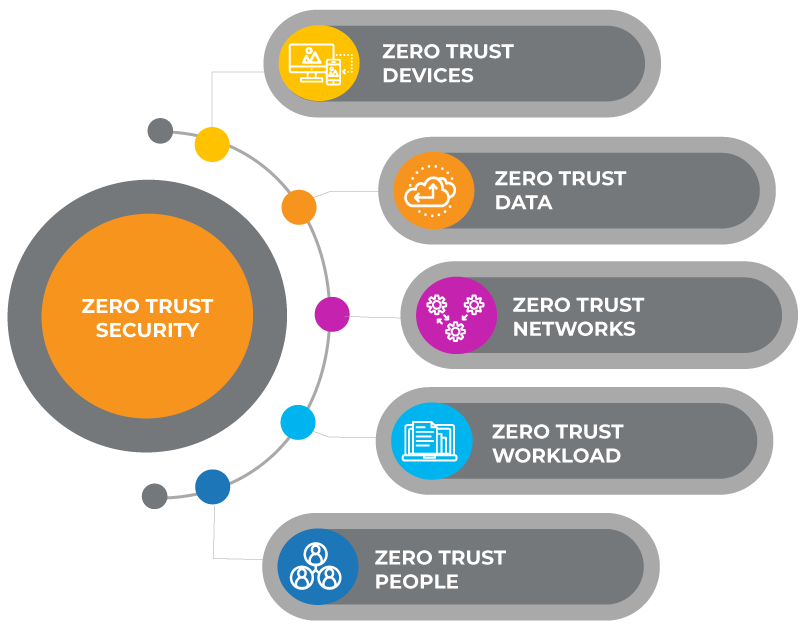
ix. The Principles of Zero Trust
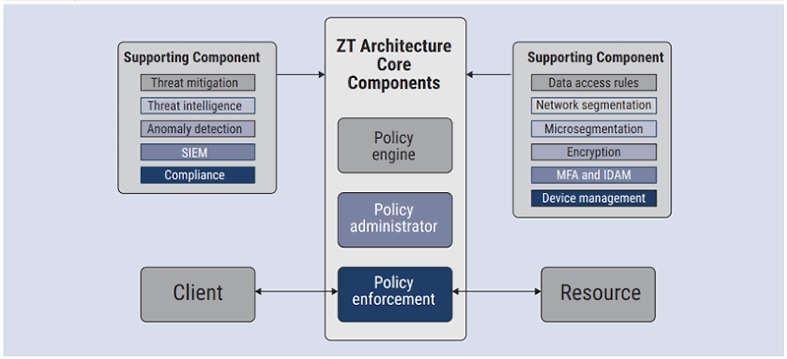
Zero Trust addresses these vulnerabilities by eliminating the concept of trust from the organization’s network architecture. Under this model, no entity, whether inside or outside the network, is trusted by default.
Access to resources is granted based on strict identity verification, least privilege access, and micro-segmentation policies, regardless of the user’s location.
A. Stringent Access Control: Access to resources is restricted to what is necessary for specific roles and tasks. This minimizes the potential impact of a breach by ensuring that even if attackers gain access, they are severely limited in what they can do.
B. Multi-factor Authentication (MFA): Zero Trust mandates robust authentication mechanisms, including MFA, ensuring that stolen credentials alone are insufficient for gaining access to critical resources.
C. Continuous Monitoring and Validation: Trust levels are dynamically adjusted based on continuous monitoring of user behavior and device security posture, ensuring that any anomalous activity triggers immediate action.
x. Benefits of Zero Trust

A. Enhanced Security Posture: By assuming that threats can originate from anywhere and ensuring rigorous verification, Zero Trust significantly reduces the attack surface and enhances the organization’s defense against both internal and external threats.
B. Improved Compliance Posture: The detailed access controls and monitoring capabilities integral to the Zero Trust model help organizations meet regulatory and compliance requirements more effectively, protecting against data breaches and their associated penalties.
C. Flexibility and Scalability: Zero Trust is inherently adaptable, accommodating new technologies and work practices, such as cloud computing and remote work, thereby supporting the organization’s growth and digital transformation initiatives.
D. Decreased Complexity and Costs: By simplifying security infrastructure and reducing the reliance on complex, perimeter-based defenses, organizations can potentially lower their operational costs and improve security efficacy.
xi. Conclusion
The migration towards a Zero Trust model is a strategic response to a changing security landscape, marked by sophisticated cyber threats, insider risks, and the evolving nature of work and technology.
By adopting a Zero Trust approach, organizations not only fortify their defenses against a broad spectrum of threats but also align their security practices with the demands of the modern digital world.
This transition is not merely a trend but a necessary evolution in the ongoing effort to protect the integrity, confidentiality, and availability of critical resources in an increasingly interconnected environment.
Moreover, the Zero-Trust model aligns with the principle of least privilege, ensuring that users have the minimum level of access necessary to perform their duties. This principle helps contain potential threats by limiting the impact of a compromised account, reducing the chances of lateral movement within the network.
xii. Further references
SponsoredLogRhythmhttps://www.logrhythm.comRead the Forrester Report
The Benefits of Adopting a Zero Trust Security Model for Your Company – LinkedIn
CDWhttps://www.cdw.com › security › g…Evolving the Zero-Trust Security Model for Business
csoonline.comwww.csoonline.com9 in 10 organizations have embraced zero-trust security globally
ColorTokenscolortokens.com10 Reasons Why Enterprises Need Zero Trust Security
Portnoxhttps://www.portnox.com › zero-tru…How Is the Zero Trust Model Being Implemented Today?
CyberArkhttps://www.cyberark.com › blogWhat Is Zero Trust and Why Is it So Important?
